Agents Are Hiring Humans. Who Is Securing the Them?
5 February 2026

5 February 2026

5 February 2026

5 February 2026
Continuous posture management and real-time alerts reduce the risk of attack and prevent connections to unauthorized servers.
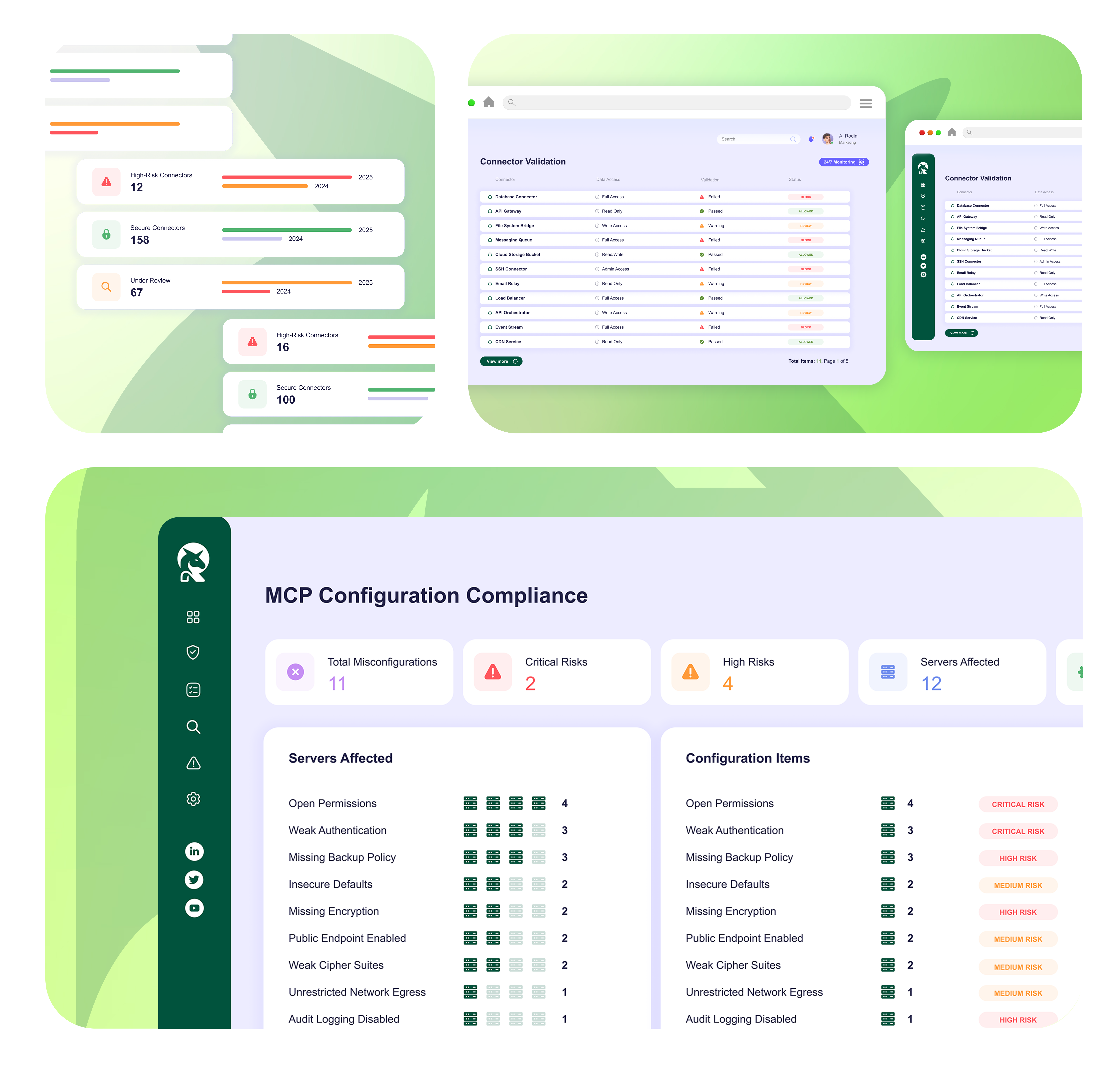

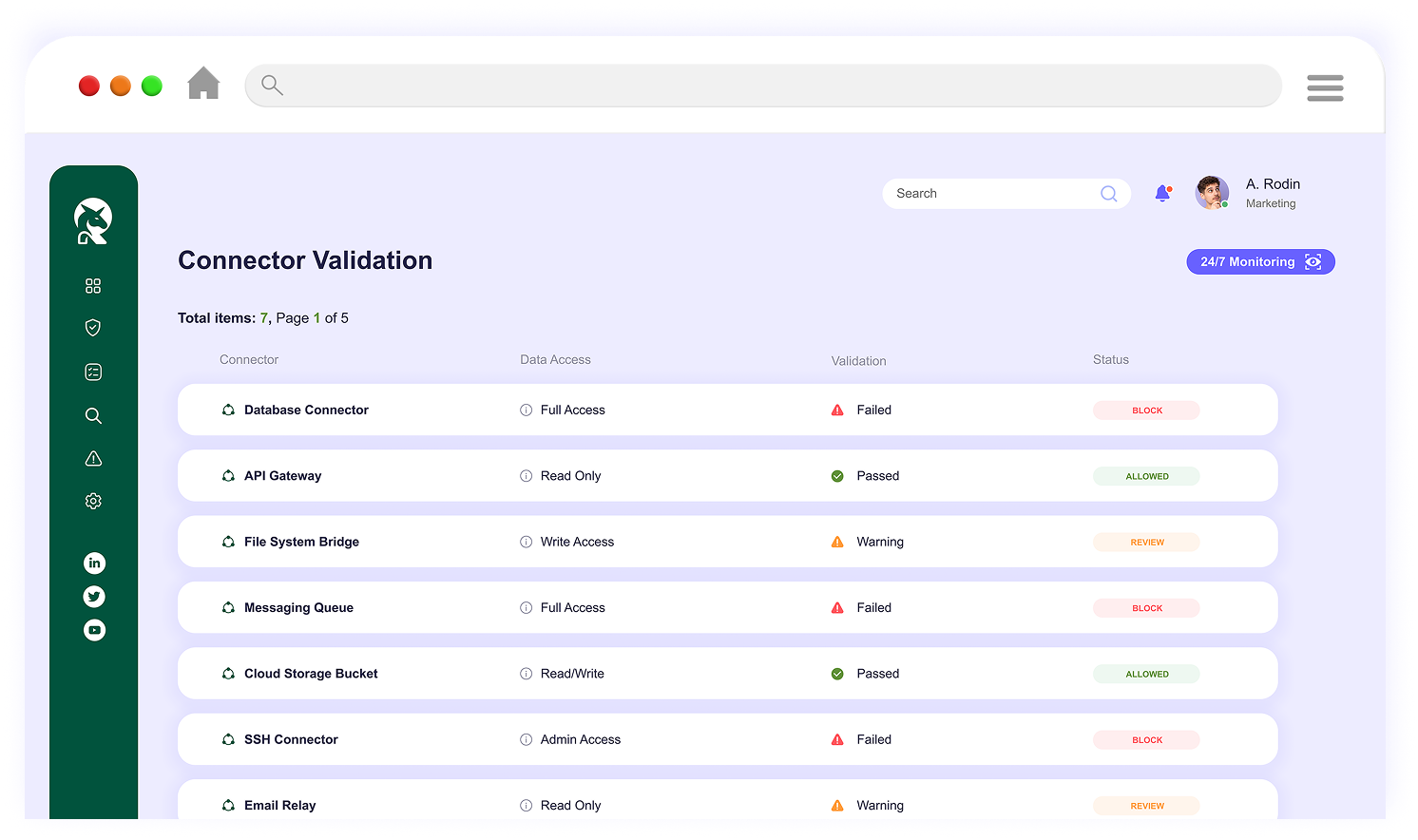
Kirin maintains an up-to-date inventory of MCP servers and validates every connection, blocking rogue or malicious servers before they gain access.
Kirin continuously monitors MCP settings and permissions, alerting on misconfigurations and policy drift that could open hidden entry points.

By validating MCP connections, Kirin keeps tools like GitHub Copilot, Cursor, and ClaudeCode safe from unauthorized access and malicious activity.
Keeps MCP servers aligned with secure baselines
Maintains an updated list of allowed servers
Flags deviations from policy or misconfigurations as they occur
Enriches detections with feed data and incident reports

Because they connect directly into enterprise systems, misconfigurations or rogue connectors can give attackers hidden access paths.
By enforcing secure configs, maintaining server inventories, and flagging unapproved connectors in real time.
No. Guardrails run in the background, allowing safe adoption without blocking automation.
IAM governs identity and access; DLP watches content. Kirin uniquely protects the integration layer where agents and servers connect.
Yes. Threat intelligence updates keep detections current with emerging MCP risks.
Kirin enforces secure configurations, monitors server posture, and blocks unapproved connectors, giving enterprises the confidence to scale MCP automation safely.
United States
205 Van Buren St,
Herndon, VA 20170
Get the latest research, tools, and expert insights from Knostic.