Agents Are Hiring Humans. Who Is Securing the Them?
5 February 2026

5 February 2026

5 February 2026

5 February 2026
AI agents are great for productivity, but they can create hidden security gaps. Knostic enforces guardrails to prevent leaks and misuse.
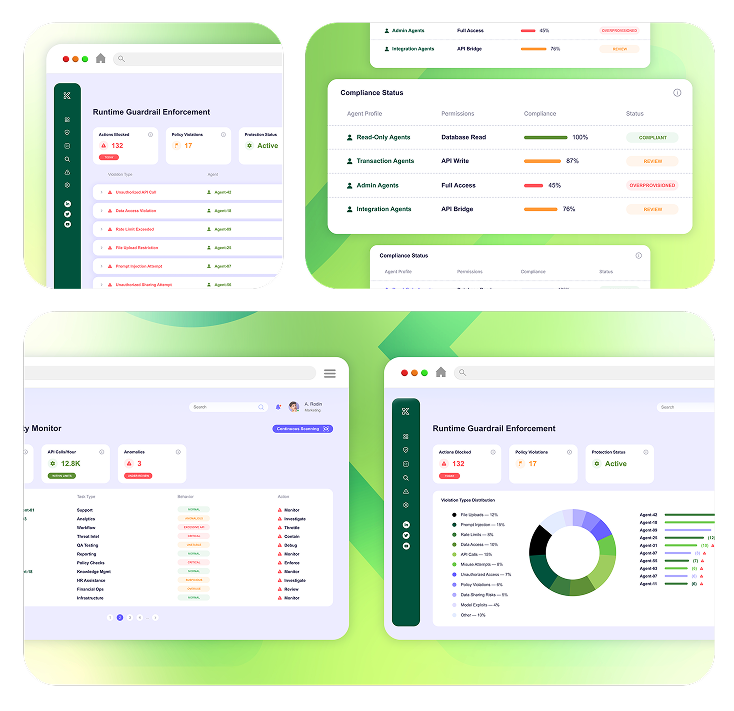

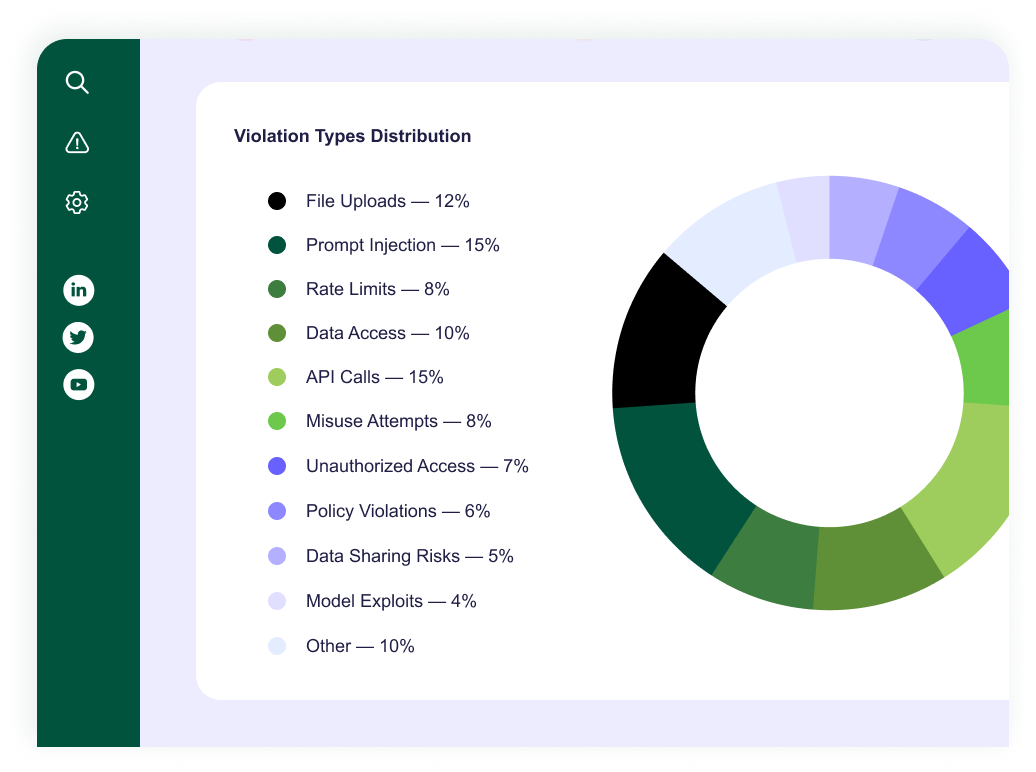
Kirin applies strict least-privilege policies so AI agents can only reach the data and APIs required for their tasks, nothing more.
Kirin continuously observes agent activity, detecting anomalies and stopping unsafe behavior before it leads to data leakage or system misuse.

Kirin identifies malicious instructions and prompt injection attempts targeting agents, blocking harmful actions before they can trigger damage.
Enforce OAuth-based agent authentication
Map agent roles to privileges and enforce need-to-know boundaries
Track every agentic action and stop unsafe behavior in real time
Block malicious instructions targeting agents
Apply consistent enforcement across SaaS, in-house, and MCP agents
Maintain logs for compliance and incident response

They can act autonomously, overreach permissions, follow malicious instructions, or trigger unvetted workflows, leading to data leakage or disruption.
By enforcing least-privilege profiles, monitoring runtime behavior, and blocking unsafe or anomalous actions in real time.
No. Guardrails ensure agents complete tasks safely, without overstepping or compromising systems.
Audit logs and runtime monitoring provide evidence for compliance, incident response, and policy enforcement.
Yes. AS secures in-house, SaaS-based, and MCP-driven agents with consistent policies across all.
Kirin enforces guardrails for autonomous AI agents, with least-privilege access, runtime monitoring, and policy enforcement so enterprises can innovate without compromise.
United States
205 Van Buren St,
Herndon, VA 20170
Get the latest research, tools, and expert insights from Knostic.