Agents Are Hiring Humans. Who Is Securing the Them?
5 February 2026

5 February 2026

5 February 2026

5 February 2026
Knostic pinpoints critical exposures in real time and streamlines governance across the enterprise.
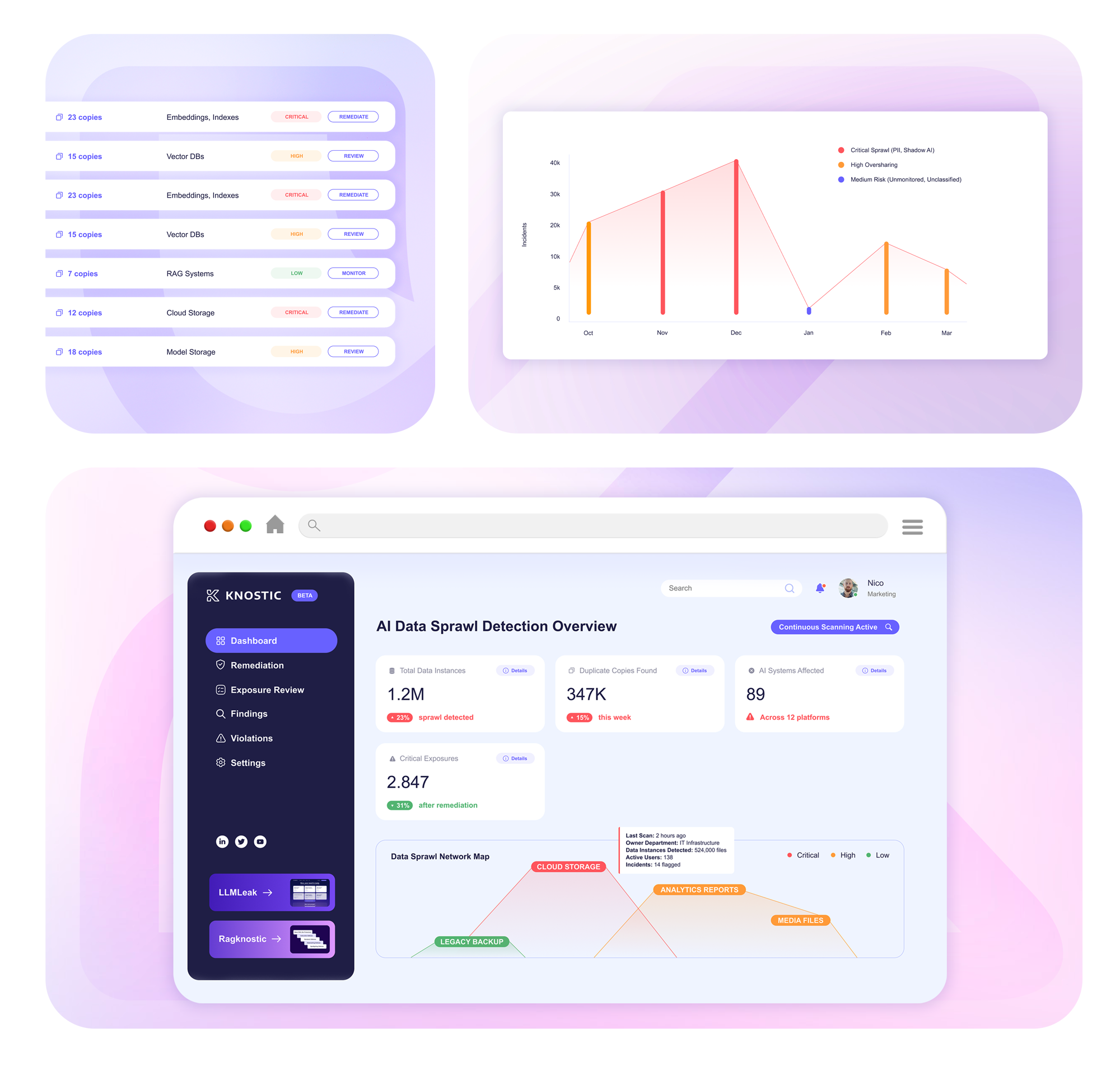

Knostic uses AI to locate duplicated, archived, or misplaced data. It reveals exposures traditional tools miss across embeddings, vector stores, indexes, and SaaS exports.
Knostic identifies ownership, traces data lineage, and visualizes who can access each copy, giving teams clarity and accountability for every exposure.

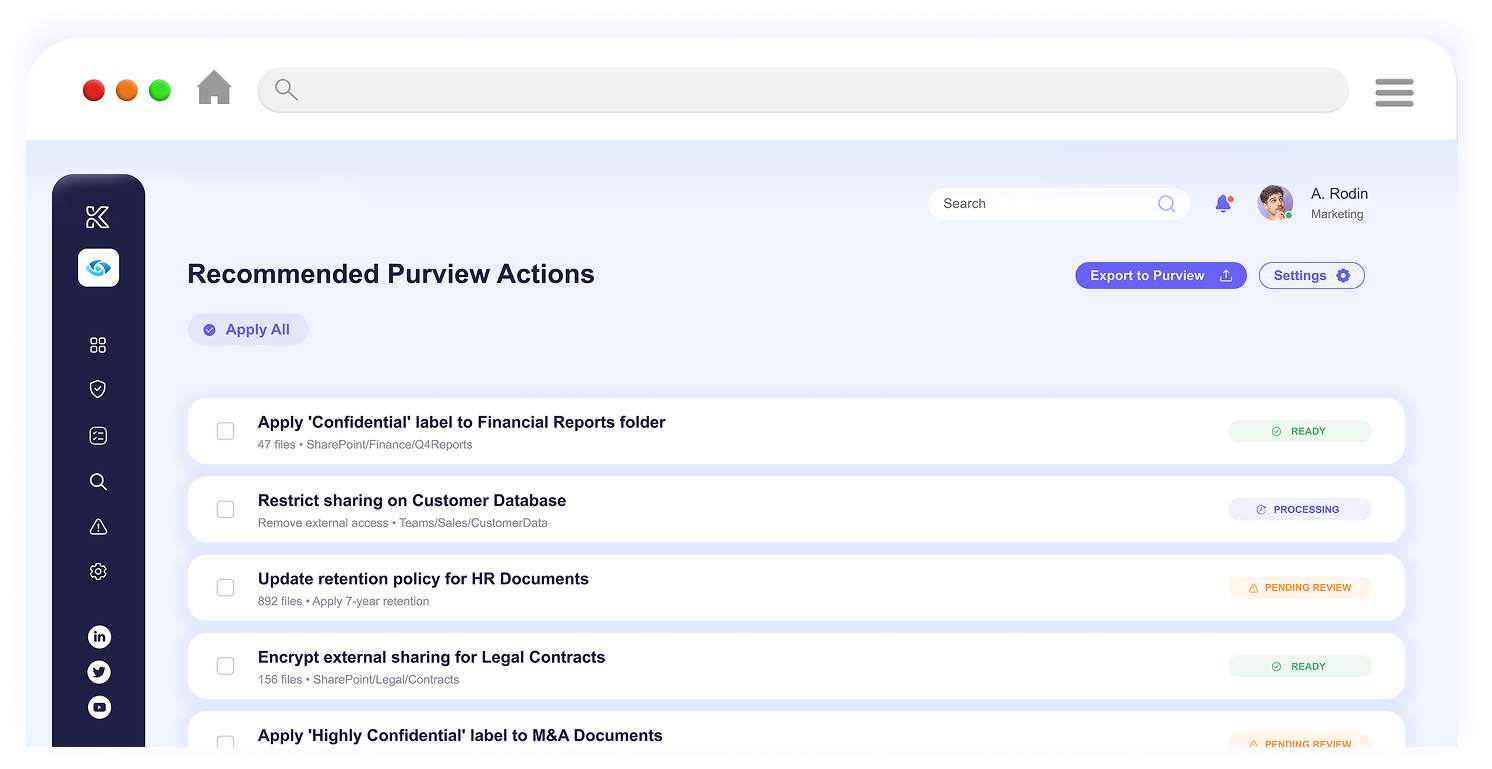
Tighten permissions and apply labels where most needed. Knostic ranks exposures by sensitivity and business impact, then guides teams to remediate with targeted fixes.
Map sensitive data across embeddings, indexes, caches, and SaaS exports
Model least-privilege access by role and flag exposures beyond business need
Identify true content owners and trace propagation paths for accountable cleanup.
Focus effort on exposures with the greatest business and compliance impact
Tailored advice for adjusting permissions, retention, and labeling to control sprawl

AI multiplies data copies across embeddings, indexes, and caches, creating uncontrolled propagation that permissions-based security tools can’t track.
By unifying exposure mapping into a living data map, ranking risks by impact, and providing AI-generated remediation guidance.
DSPM often floods teams with false positives. Knostic focuses on AI-specific systems and applies persona-based context to prioritize real exposure.
No. It accelerates adoption by giving security teams clear visibility and remediation that’s fast, targeted, and repeatable.
Yes. It complements Oversharing Management and Data Labeling, creating an end-to-end framework for AI-ready data governance.
Knostic keeps your AI adoption remains secure and compliant. It discovers hidden copies of sensitive data, maps access and ownership, and guides teams to remediate high-impact risks.
United States
205 Van Buren St,
Herndon, VA 20170
Get the latest research, tools, and expert insights from Knostic.