Agents Are Hiring Humans. Who Is Securing the Them?
5 February 2026

5 February 2026

5 February 2026

5 February 2026
Detect shadow AI and enhance Purview to enable secure, compliant AI use across your workforce.
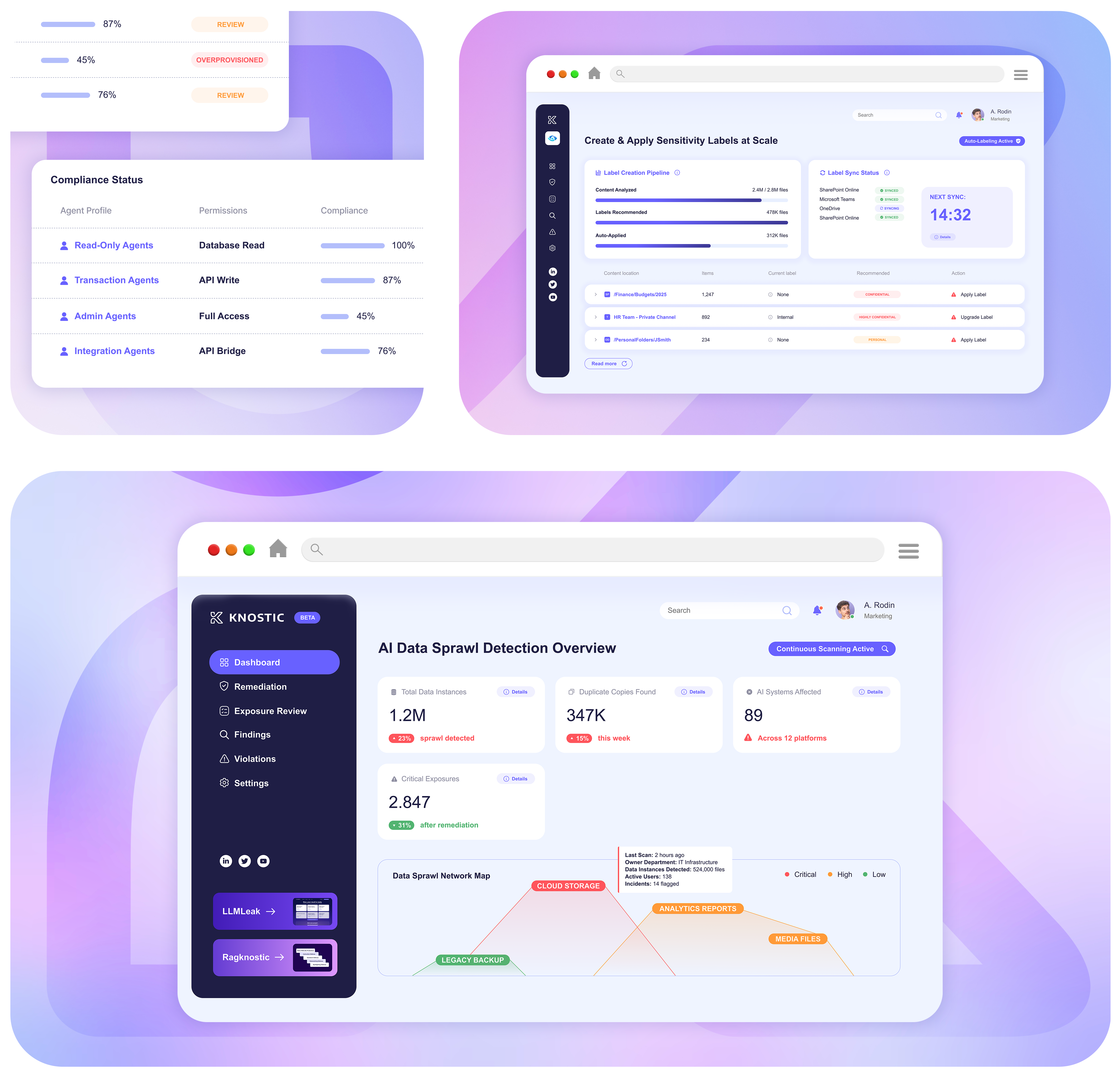
Knostic identifies unauthorized or unsanctioned AI assistants in use across the enterprise, giving you visibility to prevent data leaks and enforce policy.
Strengthen Purview with automated labeling, oversharing detection, and accelerated remediation. Get more value from E3 and E5.
No. Knostic enhances Purview by adding real-time oversharing detection, automated labeling, and remediation while Purview remains your system of record.
Yes. Knostic integrates with both Purview E3 and E5, helping you maximize the value of either license tier.
Most organizations see initial results in hours. Knostic requires only a few credentials and works alongside existing Microsoft 365 infrastructure.
No. It builds on your existing Purview policies and audit processes, so teams maintain the same workflows while gaining stronger visibility and control.
Meaningful coverage is achieved in weeks, not months, thanks to automation and prioritization by risk.
Knostic helps you spot Shadow AI activity before it puts data at risk and strengthen Purview E3 and E5 with automated labeling, oversharing detection, and streamlined remediation.
United States
205 Van Buren St,
Herndon, VA 20170
Get the latest research, tools, and expert insights from Knostic.