How to Build a Shadow AI Detection Program in 90 Days
26 January 2026
26 January 2026

21 January 2026

20 January 2026

19 January 2026
Get more from your Purview, E3, and E5 Investments with Knostic.
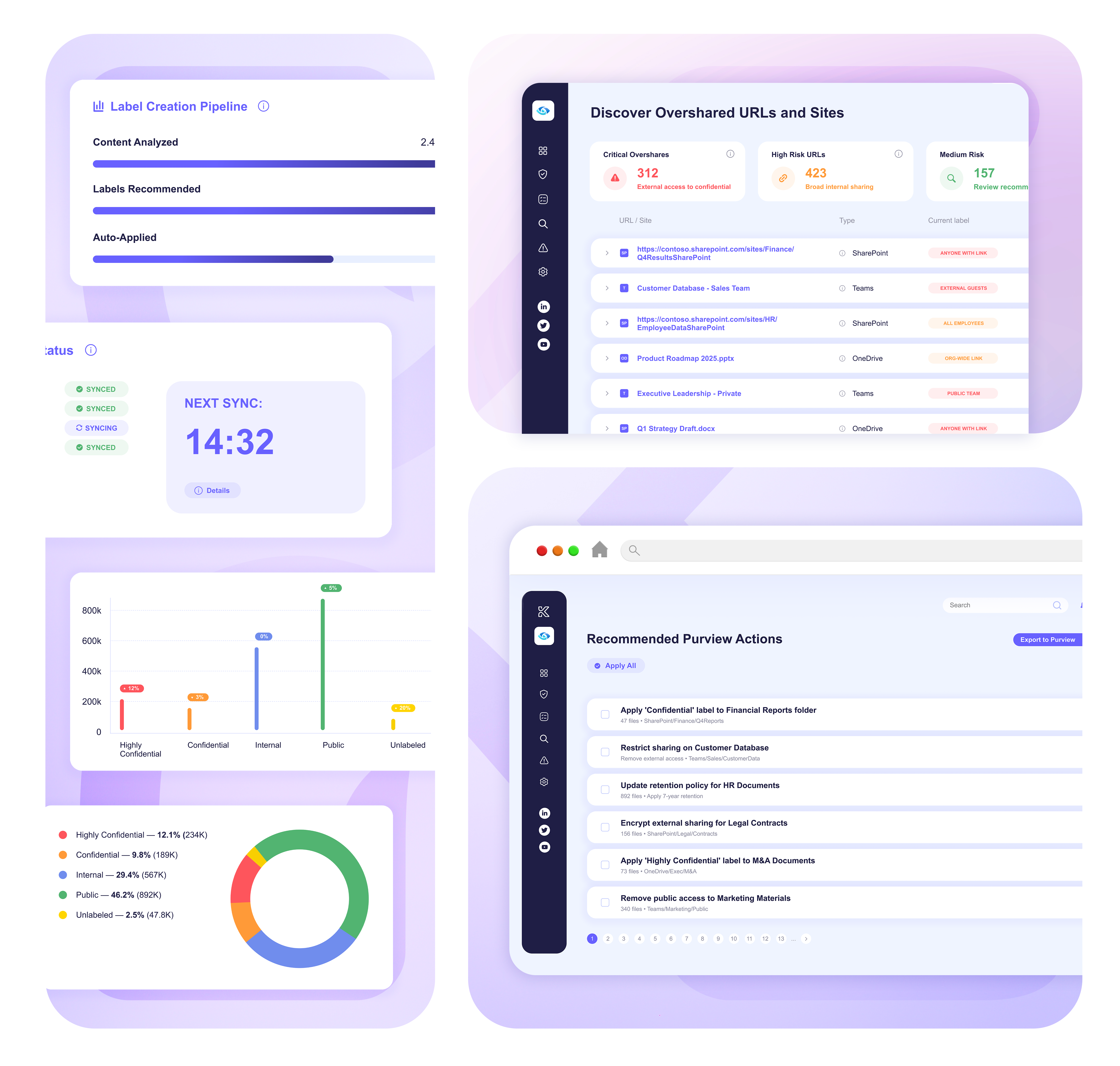

Knostic scans logs, APIs, and integrations to detect every AI tool, sanctioned or not. You can see exactly who is using what.
Based on real usage patterns, Knostic applies or recommends sensitivity labels so DLP and Purview policies enforce the right protections.

Streamlined remediation keeps access aligned with business need. Knostic tightens permissions, updates labels, and triggers workflows with one click.
Identify exposed files, folders, and links across Microsoft 365 and Teams
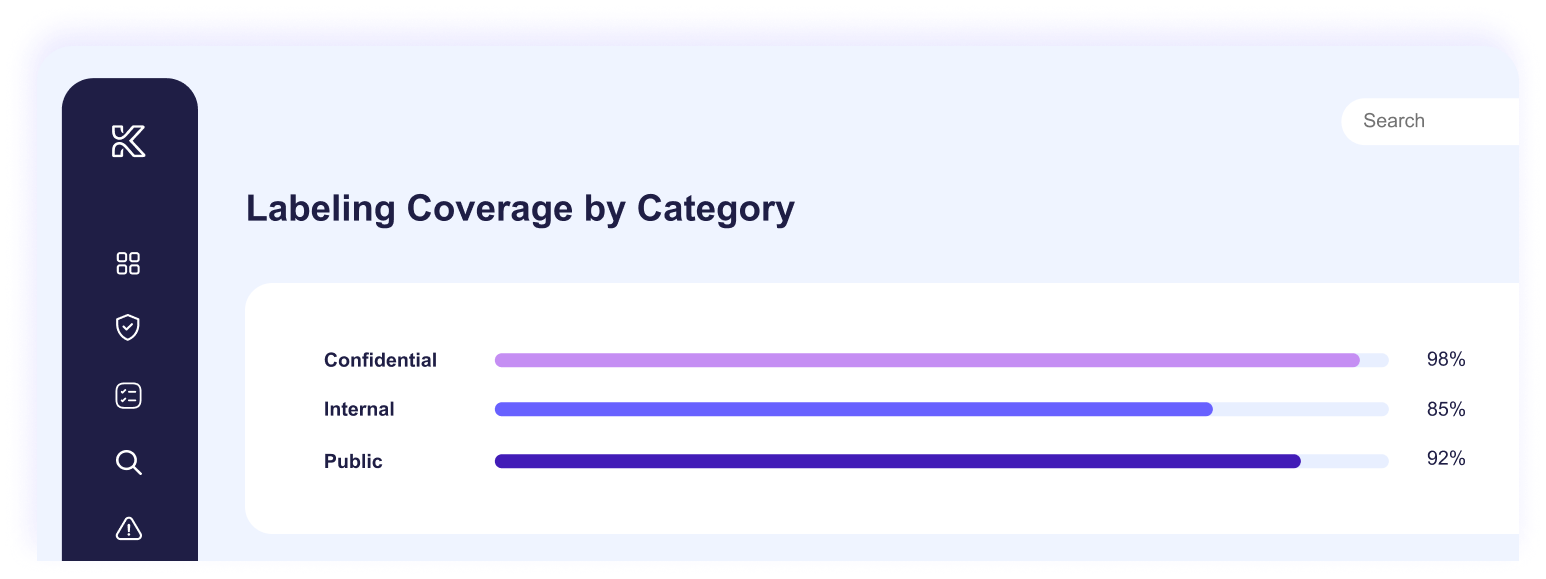
Apply labels where risk is highest to strengthen Purview and DLP controls
Right-size access with guided fixes and automated policy updates
Detect new oversharing and policy drift in real time
Provide audit-ready evidence of data governance improvements

Knostic detects overshared files and misconfigured access, then automatically applies or recommends sensitivity labels so Purview and DLP controls work as intended.
Yes. It can tighten permissions, update sharing links, and trigger automated workflows to keep access aligned with business needs.
Most organizations see actionable findings in hours and achieve measurable risk reduction within days.
No. Knostic enhances Purview by filling gaps, accelerating labeling, and improving the effectiveness of existing Microsoft investments.
Yes. Knostic provides ongoing monitoring and real-time alerts when new data exposure or permission drift occurs.
Absolutely. Knostic is built for enterprise scale, supporting complex environments with millions of files and users.
AI Data Governance makes Purview faster, smarter, and AI-ready, and helps strengthen your governance foundation without changing your system of record.
United States
205 Van Buren St,
Herndon, VA 20170
Get the latest research, tools, and expert insights from Knostic.